In today’s world, securing your Remote Desktop Protocol (RDP) environment is crucial. Hackers constantly scan for open ports to exploit, and RDP servers are often a prime target. But what if you could make your RDP environment invisible to hackers? In this article, we’ll show you how to do just that using our innovative product, SSHepherd®.
The Problem with Open RDP Ports
Remote Desktop Protocol (RDP) is a powerful tool that allows users to connect to and manage their Windows servers remotely. However, this convenience comes with significant security risks. RDP operates by connecting through open network ports, typically port 3389, on the Windows server. These open ports act as entry points, not just for legitimate users, but also for malicious actors.
Why Open Ports Are Vulnerable
When you have open RDP ports, they are essentially gateways into your network. Hackers constantly scan the internet for these open ports using automated tools. Once they find an open port, they can launch various types of attacks, such as:
- Brute Force Attacks: Hackers use automated scripts to repeatedly guess the username and password combinations until they find the correct one. Given enough time, even strong passwords can eventually be cracked.
- Credential Stuffing: If hackers have obtained login credentials from other breaches, they can try these known combinations on your RDP server, hoping that users have reused passwords across different platforms.
- Exploiting Vulnerabilities: Hackers can also exploit known vulnerabilities in the RDP protocol or the Windows operating system. If your system is not regularly updated with the latest security patches, it becomes an easy target.
The Consequences of a Breach
If a hacker successfully gains access through an open RDP port, the consequences can be devastating. They can:
- Install Malware: Deploy malicious software, including ransomware, which can encrypt your files and demand a ransom for their release.
- Data Theft: Access sensitive data stored on your servers, leading to data breaches and potential regulatory fines.
- Network Control: Take control of your entire network, allowing them to move laterally and compromise other systems and services.
Traditional Security Measures Fall Short
Traditional security measures, such as firewalls and antivirus software, are often not enough to fully protect open RDP ports. While they can block known threats, they struggle to keep up with the constantly evolving tactics of cybercriminals. This is why it is crucial to go beyond these measures and implement more robust solutions like SSHepherd®.
By addressing the inherent vulnerabilities of open RDP ports, SSHepherd® provides a proactive approach to securing your remote connections, making it significantly harder for hackers to even detect, let alone breach, your network.
SSHepherd: Your RDP Hardening Solution
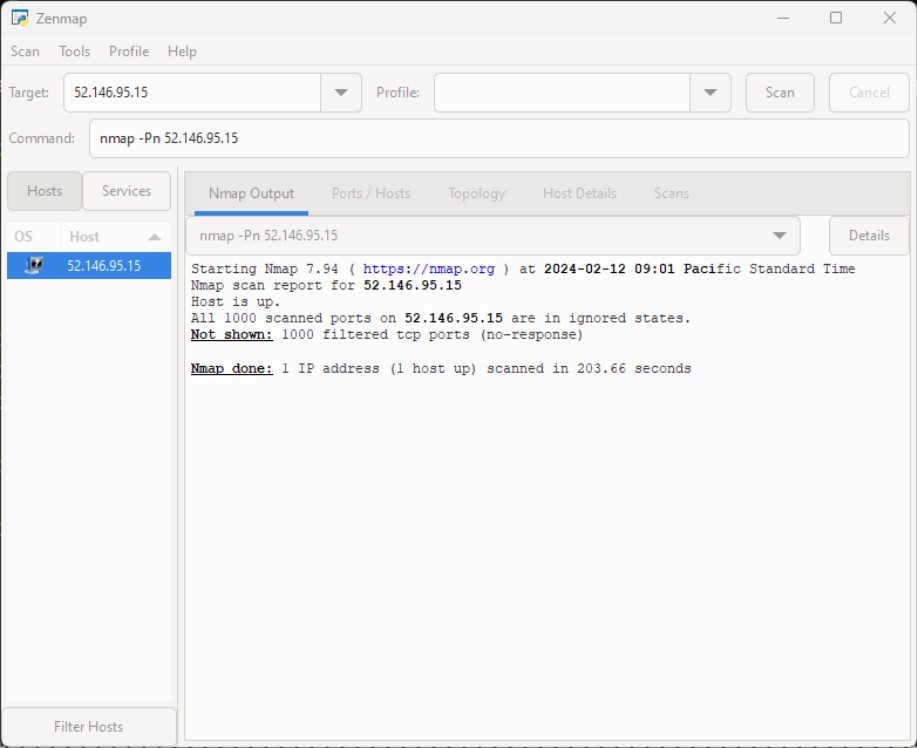
SSHepherd® offers a secure connection to your RDP servers while keeping the ports completely turned off. As you can see from the Zenmap scan, hackers have nothing to scan, effectively rendering your RDP environment invisible.
Yet, through SSHepherd®, you can launch a native RDP session while keeping the ports entirely closed.
To see a demo of SSHepherd working over a RDP connection:
