
February 18, 2026
The “Invisible” Revolution: Why Your Network’s Open Ports Are the New Phishing
According to the 2025 Verizon Data Breach Investigations Report (DBIR), vulnerability exploitation—the act of targeting unpatched software and open network ports—has surged by 34%....

January 15, 2026
Implementing Zero Trust in Active Directory Through GPO Change Management
Platforms like UPA extend secure change control beyond traditional Windows domains to hybrid, cloud, and even non-domain-joined systems, helping you maintain consistent governance as your...
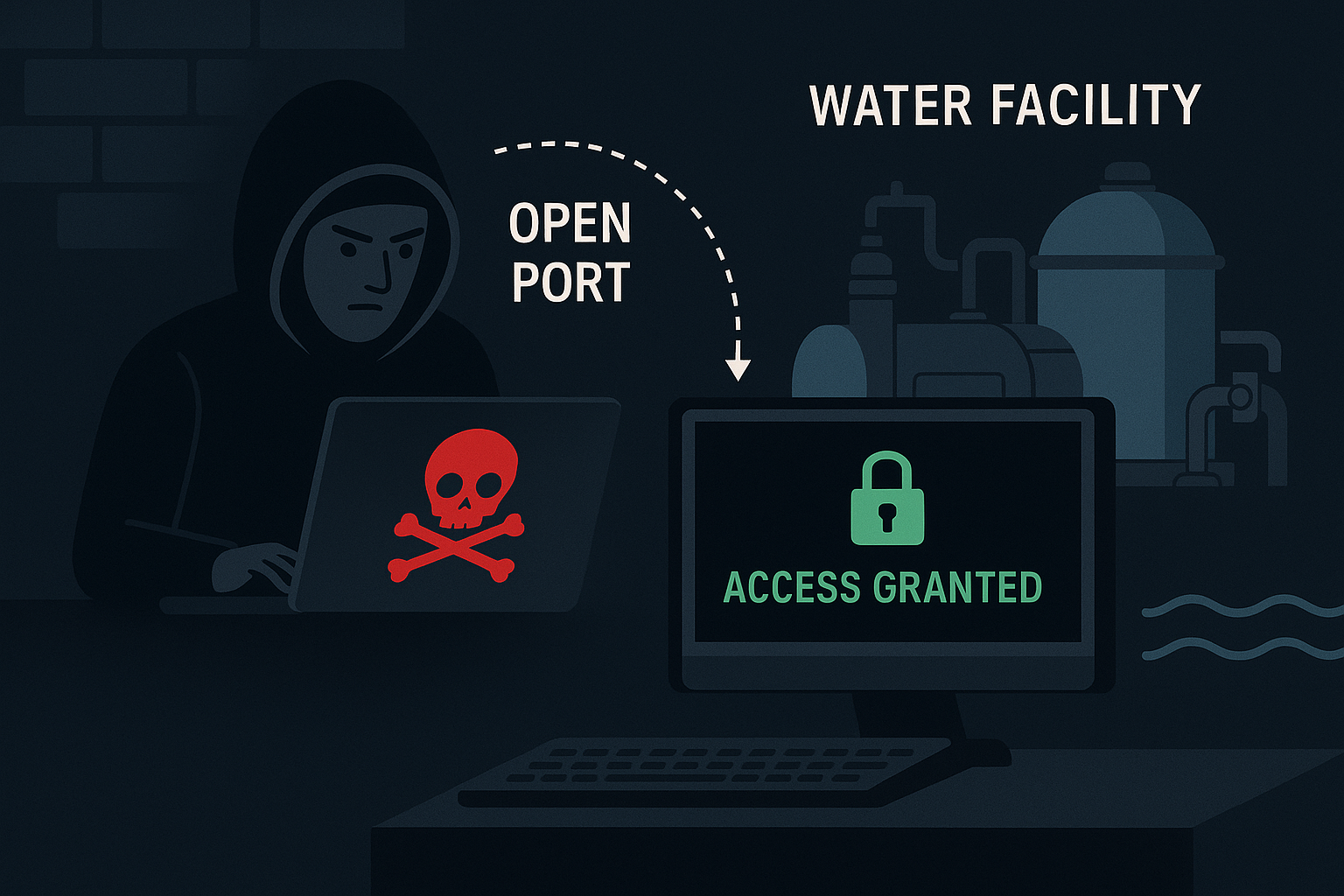
November 19, 2025
The Silent Threat: Why America’s Critical Infrastructure is Under Attack
As the attack surface expands—from industrial control networks to cloud-connected IoT sensors—traditional perimeter defenses no longer suffice. Security teams must assume compromise and reduce exposure...

October 22, 2025
Evaluating Your Next Group Policy Management Solution: Key Considerations for Enterprise AD Administrators After AGPM
Microsoft’s Advanced Group Policy Management (AGPM) has been the cornerstone of Group Policy change control for more than a decade. It gave enterprise administrators versioning,...

September 17, 2025
Hacker Exploits and GPOs: The Unseen Attack Vector in Your Active Directory
Group Policy Objects (GPOs) are essential for managing a secure Active Directory (AD) environment. They are a powerful administrative tool used to deploy settings, enforce...
August 19, 2025
Time to Modernize Your Group Policy Management
This blog dives into why MMC and GPMC fall short and how Full Armor’s Universal Policy Administrator (UPA) web-based platform revolutionizes GPO workflows....

July 15, 2025
The Hidden Vulnerability in Your IT Infrastructure: Why Open Ports Are Your Biggest Security Risk
By addressing the open port visibility problem, SSHepherd® helps organizations eliminate what many security experts consider the number one mistake leading to successful breaches. When...
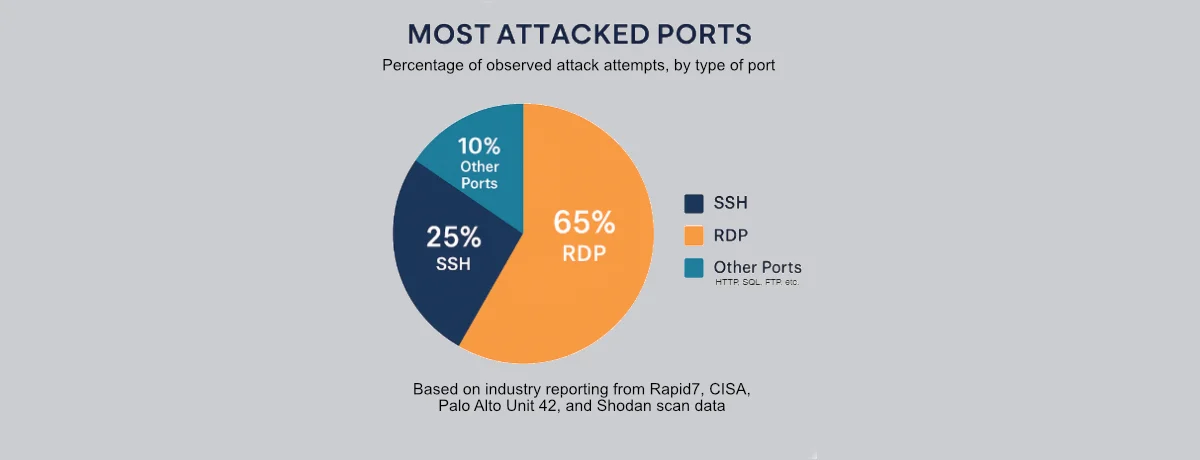
June 3, 2025
The 2 Most Dangerous and Attacked Ports in Your Environment
Industry reports consistently identify RDP and SSH as the most frequently attacked ports on the internet. Recent Shodan scans reveal the staggering scope of this...

April 9, 2025
Make Your Network Traffic Invisible to Hackers with SSHepherd
Traditional security measures like firewalls and encryption play a critical role, but they aren’t enough. If a hacker can see your ports, they can target...

April 9, 2025
How to Make MySQL Databases Invisible to Hackers with SSHepherd
When it comes to securing MySQL databases, most organizations are focused on encryption, firewalls, and authentication layers. But there’s one glaring risk that’s often overlooked:...

March 14, 2025
Making Your Websites Invisible to Hackers, Bots, and AI
As cybersecurity threats become more sophisticated, businesses of all sizes face an ongoing challenge: how do you keep sensitive websites and internal applications secure from...

February 12, 2025
Revolutionize GPO Management: Preparing for AGPM’s End-of-Life and Beyond
As enterprises navigate the evolving landscape of IT infrastructure management, a significant milestone approaches that demands immediate attention: Microsoft’s Advanced Group Policy Management (AGPM) will...

January 15, 2025
How SSHepherd® Locks Down SSH Ports and Reduces Cybersecurity Risks
Cybersecurity professionals face an ongoing challenge: balancing the accessibility of network systems with the need to minimize vulnerabilities. Open SSH ports, critical for managing servers...

December 11, 2024
Invisible Fortresses: Securing Microsoft IIS Servers with SSHepherd
Microsoft Internet Information Services (IIS) powers countless critical web applications, from e-commerce platforms to internal business tools. As one of the most widely used web...

November 14, 2024
Invisible Fortresses: How SSHepherd Revolutionizes SFTP Server Security
In today’s digital landscape, the security of file transfers is paramount for organizations across all industries. Many businesses rely on SSH File Transfer Protocol (SFTP)...

October 17, 2024
UPA’s Role-Based GPO Change Management: Flexible, Offline, and Mission Critical
With the growing demand for cross-platform consistency and security, Universal Policy Administrator (UPA) steps in as a comprehensive solution to manage GPOs, ensuring flexibility, regulatory...
September 27, 2024
The Evolution of Microsoft Active Directory Group Policy Objects and the Future of GPO Management
The Advent and History of Group Policy Objects Introduced with Windows 2000, Group Policy Objects (GPOs) revolutionized IT administration by providing centralized management for users...

August 30, 2024
Introduction to Linux Security Risks
Linux serves as the backbone behind most of the internet. Its widespread use makes it a prime target for hackers aiming to exploit vulnerabilities....
August 14, 2024
Understanding Insider Threats and How to Stop Them with SSHepherd
Insider threats pose one of the most challenging security risks for organizations today. Unlike external attacks, insider threats come from within the organization, making them...

July 26, 2024
Enhancing Cybersecurity with SSHepherd: A Comprehensive Mapping to NIST 800-53 Controls
SSHepherd, a powerful cybersecurity product, offers a range of features that map directly to multiple control families within NIST 800-53, enabling organizations to strengthen their...
