
Microsoft’s Advanced Group Policy Management (AGPM) has been the cornerstone of Group Policy change control for more than a decade. It gave enterprise administrators versioning, check-in/check-out, and approval workflows long before “change management” became a mainstream security requirement.
But with AGPM reaching end of life in April 2026, enterprises that rely on it face a critical decision: what comes next?
If you manage Group Policy Objects (GPOs) in Active Directory, this is the perfect time to step back and evaluate what your organization truly needs in a modern GPO management solution—one that aligns with today’s hybrid, compliance-driven environments.
Why Organizations Are Reassessing GPO Management Now
Several converging trends are forcing IT teams to modernize:
- End of Support for AGPM: After April 2026, AGPM will no longer receive updates or compatibility fixes. Unsupported tools quickly become liabilities—especially those touching domain-level configurations.
- Evolving Compliance Mandates: Frameworks such as CIS, NIST 800-53, HIPAA, and SOX now require verifiable audit trails, controlled change processes, and the use of supported software.
- Hybrid Active Directory Growth: Many organizations operate a mix of on-prem AD and Entra ID (formerly Azure AD). AGPM was never built with hybrid management in mind.
- Security and Ransomware Risks: Uncontrolled GPO changes remain one of the least-monitored attack vectors inside enterprise networks.
These pressures mean it’s no longer enough to “just manage GPOs.” Administrators need tools that enforce accountability, transparency, and recovery.
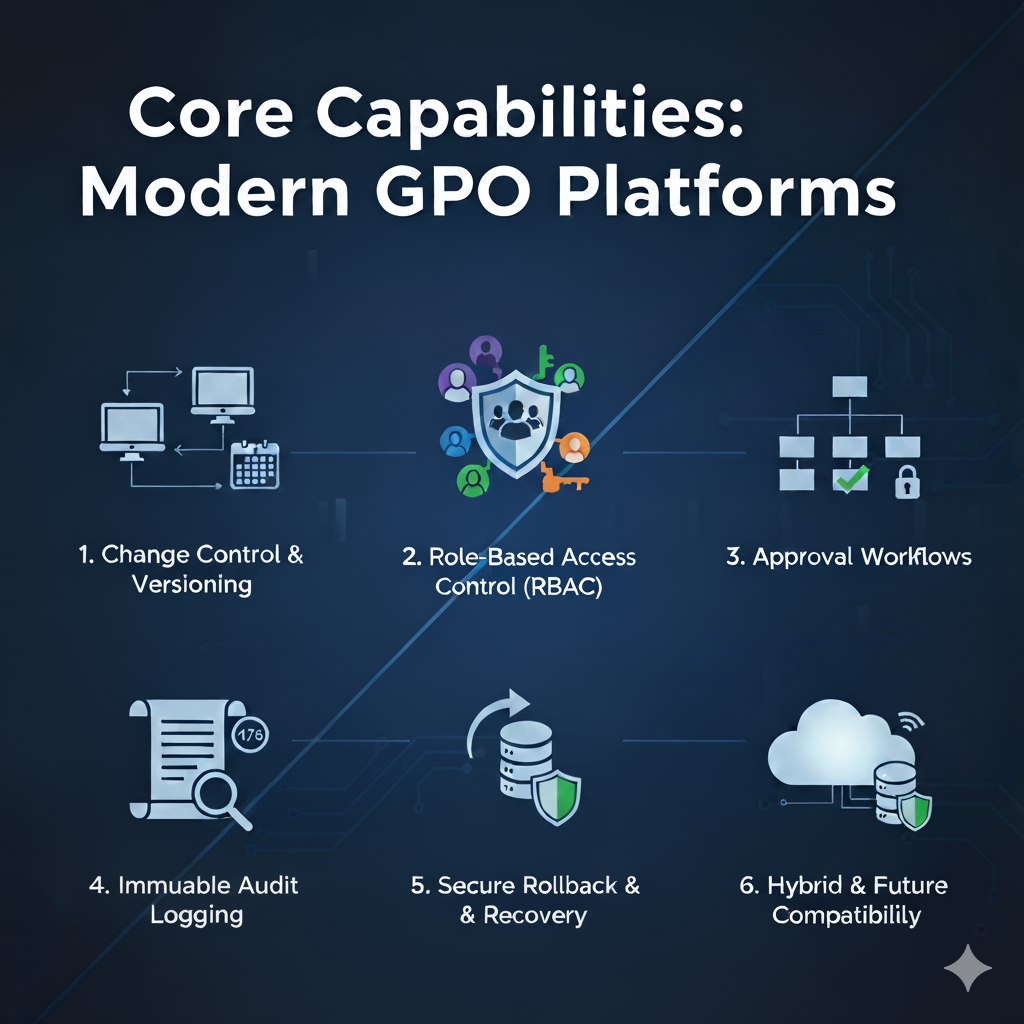
Core Capabilities Every Modern GPO Platform Should Provide
When evaluating AGPM replacements or successors, look for capabilities that go beyond simple versioning.
1. Change Control and Offline Versioning
A modern solution should allow administrators to manage and stage GPOs offline before deployment. Offline repositories—ideally backed by SQL or similar databases—enable secure editing, review, and rollback without impacting production AD until approved.
2. Role-Based Access Control (RBAC) and Delegation
Fine-grained permissions are essential. Delegating access by OU, team, or role reduces risk while maintaining flexibility. RBAC also aligns with zero-trust principles, ensuring each administrator only has the access necessary for their function.
3. Approval Workflows
A structured check-in/check-out process ensures that no change is pushed live without review. Look for configurable workflows that support multiple reviewers or approvers—especially in regulated industries.
4. Immutable Audit Logging
Auditability is key to compliance. Your chosen platform should record every action—who made it, when, what changed, and why. Immutable logs make it possible to prove due diligence during audits or incident investigations.
5. Secure Rollback and Recovery
Accidental or malicious GPO changes can cripple an environment. Instant rollback capability—reverting to a known-good state—should be a non-negotiable feature in any AGPM replacement.
6. Hybrid and Future Compatibility
Ensure that the solution supports modern Windows versions and hybrid Active Directory architectures. As Microsoft evolves Entra ID and introduces cloud-based policy control, flexibility will be key.
Risks of Staying on Legacy or Unsupported Tools
Remaining on AGPM beyond its end of life introduces tangible risks:
- Security Vulnerabilities: No future security patches means potential exploit paths stay open indefinitely.
- Compliance Exposure: Many auditors view unsupported software as a control failure. Using AGPM past 2026 could directly impact compliance certifications.
- Operational Fragility: Windows Server and AD schema updates could break AGPM functionality without warning, leaving change management processes stalled.
- No Vendor Accountability: If AGPM fails or causes a domain-level issue, Microsoft will no longer support it. The risk shifts entirely to your organization.
Even organizations that continue using AGPM temporarily should begin migration planning now to avoid rushed, high-risk transitions later.

Planning Your Migration Path
A thoughtful migration can minimize disruption while strengthening your control posture. Key steps include:
- Inventory and Baseline: Export and document all existing GPOs, delegation models, and version histories.
- Assess Current Workflows: Identify what processes AGPM handles today—approvals, versioning, delegation—and what pain points exist.
- Define Future Requirements: Build a checklist of must-haves: RBAC, offline editing, SQL storage, compliance reporting, API integration, etc.
- Pilot a Modern Solution: Test a small subset of policies using a next-generation platform such as FullArmor’s Universal Policy Administrator (UPA) in a non-production environment.
- Train and Transition: Educate administrators on new workflows, approvals, and rollback procedures before going live.
The Future of Group Policy Management
The next era of GPO management emphasizes security, automation, and accountability. Modern platforms like UPA reflect that shift with:
- Offline SQL-based repositories that safeguard policy data outside the live AD.
- Integrated version control and approvals for every GPO edit.
- Comprehensive audit trails and rollback options that align with compliance mandates.
- Role-based access and hybrid AD support, enabling safe, distributed administration.
Whether your organization ultimately chooses UPA or another platform, the key takeaway is this:
Continuing to rely on AGPM after its end of life introduces unnecessary risk. Evaluating your next Group Policy management solution today ensures your environment remains secure, compliant, and ready for what’s next.
Contact Us to find out more about Universal Policy Administrator!
