
Group Policy Objects (GPOs) are essential for managing a secure Active Directory (AD) environment. They are a powerful administrative tool used to deploy settings, enforce security policies, and manage applications across a network. But this very power makes them a prime target for attackers. For cybercriminals, a compromised GPO is the ultimate skeleton key, offering a direct path to domain-wide control. This is the unseen attack vector that many organizations fail to defend, and it’s being actively exploited by some of the most dangerous threat actors.
Furthermore, the danger of this attack vector is growing more urgent. Microsoft is ending its support for Advanced Group Policy Management (AGPM) in April 2026, which will leave many organizations without a modern GPO change management solution. Without a replacement, these companies will lose the ability to secure their GPOs, leaving them vulnerable to the very attacks described here.
How Hackers Exploit GPOs
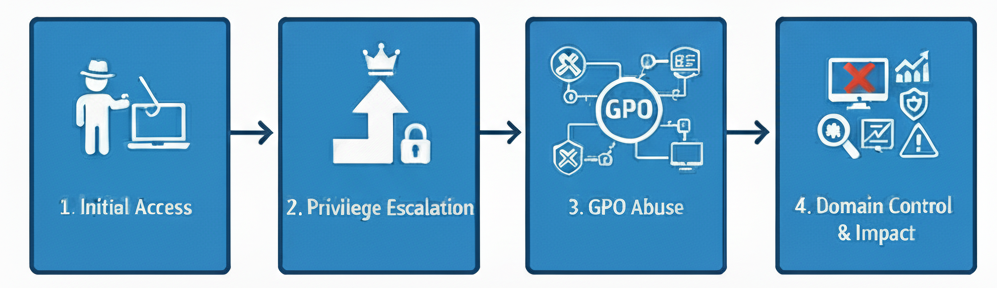
Threat actors, including notorious ransomware gangs like LockBit and BlackCat, have mastered the art of GPO exploitation. Their attacks often follow a similar, devastating pattern:
Initial Access: An attacker gains a foothold in your network, often through phishing, an unpatched vulnerability, or a misconfigured service.
Privilege Escalation: They work quickly to elevate their privileges, seeking an account with the necessary permissions to modify or create GPOs. This is a crucial step that turns a local compromise into a domain-wide threat.
GPO Abuse: Once they have the keys, they use GPOs for their malicious objectives:
- Ransomware Deployment: A common tactic is to create or modify a GPO to push malicious software across the entire network. This allows the ransomware to spread rapidly and stealthily, leveraging the trusted nature of Group Policy to evade security controls. The FBI has documented how the BlackCat (ALPHV) ransomware group has specifically used this tactic, leveraging the Windows Task Scheduler through malicious GPOs to deploy their payloads.
- Disabling Defenses: Attackers can use a GPO to disable antivirus software, turn off firewalls, or weaken other security policies. LockBit affiliates, for example, have been observed creating GPOs to disable Windows Defender and other security tools, ensuring their attacks go unimpeded.
- Establishing Persistence: By changing GPOs, hackers can ensure their malicious code runs every time a computer starts or a user logs on. This provides a persistent backdoor into the network, even after a reboot or a password change.
While GPO exploitation often leverages misconfigurations rather than a single software bug, specific vulnerabilities have been a factor. CVE-2014-1812 highlighted a critical flaw in Group Policy Preferences (GPP) where passwords could be stored insecurely, allowing an authenticated attacker to decrypt them and gain privileged access. More recently, CVE-2020-1317 described how an attacker could exploit the way Group Policy handles certain files to gain system-level privileges. These vulnerabilities, combined with the consistent use of GPOs by threat actors in real-world breaches, prove that this is a very real and present danger.
Universal Policy Administrator (UPA) Secures the Unseen Attack Vector
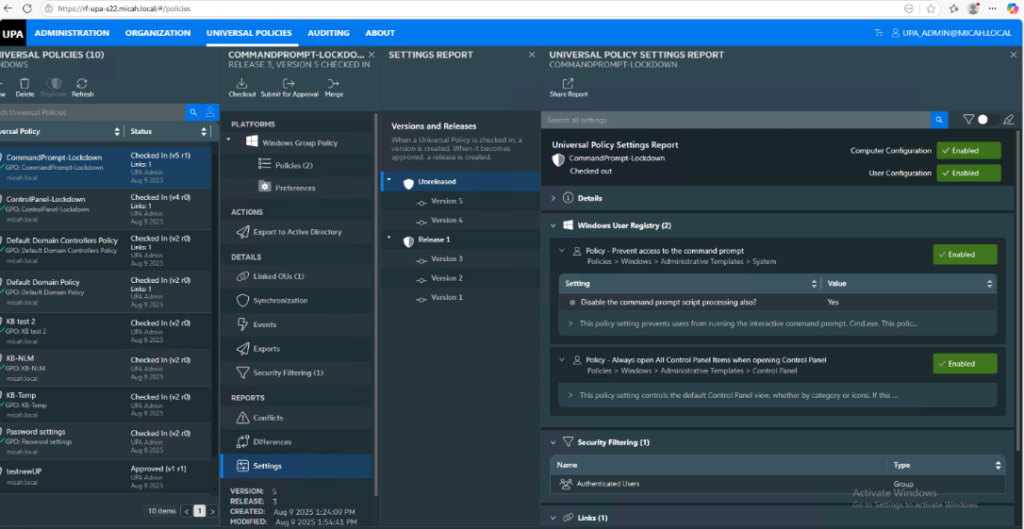
The Universal Policy Administrator (UPA) product was specifically designed to close this unseen attack vector. By taking GPOs offline into a secure environment, UPA isolates them from direct, unmonitored changes in the live Active Directory environment. This simple but powerful step prevents a compromised account from making an immediate, devastating change to your network.
The core of UPA’s defense is its rigorous change management review process. This structured workflow is key to preventing both malicious changes and the all-too-common problem of misconfigurations. These human errors, such as accidentally linking a policy to the wrong OU or using conflicting settings, can create security vulnerabilities and system instability. UPA’s process includes:
- Offline Policy Creation: Administrators create and modify GPOs in a secure, offline environment. This ensures no changes are accidentally or maliciously pushed to the live AD without proper review.
- Version Control and Audit Trails: UPA maintains a complete history of every change. You get a clear record of who made a change, when they made it, and what the change was, providing an invaluable resource for compliance and forensic analysis.
- Role-Based Delegation: You can assign granular permissions, so one team member can draft policies while another must approve them. This prevents a single compromised account from wreaking havoc and enforces the principle of least privilege.
Change Review and Conflict Detection: Before a policy is deployed, the change must be reviewed by an approver. UPA’s process helps reduce human error by requiring a second set of eyes on every change, preventing the accidental misconfigurations that often become targets for attackers.
By implementing UPA, you can eliminate the GPO as an unseen attack vector. You will enforce a disciplined, secure process that ensures every policy change is reviewed, documented, and approved before it’s deployed to the live environment. This effectively closes the door on GPO-based attacks and significantly strengthens your overall cybersecurity posture.
Contact us for more information about UPA!
