
A Leader in Cyber Security
and Policy Management
Protecting enterprises with advanced security
and comprehensive policy management

Trusted Enterprise Security Since 2000
Since 2000, we've licensed our technology to industry leaders including Microsoft, Citrix, NetIQ, LogMeIn, F5 Networks, OpenText and others. More than 5 million users and 1500 organizations rely on technology developed by Full Armor.
Whether on-premise or in the cloud, Full Armor helps Fortune 1000 companies secure and manage their IT resources.
Our Products
Universal Policy Administrator
Enterprise-grade Group Policy Management and Change Control solution for secure IT environments.
- Comprehensive policy management
- Change tracking and auditing
- Enterprise-wide deployment
SSHepherd®
Advanced stealth cybersecurity for SSH, RDP, and Applications, ensuring secure remote access and management.
- SSH and RDP protection
- Application security
- Access control management
Industry News and Our Blogs
- Our Blog
- Industry News
This is the content of the active panel
 04.09.25
04.09.25Make Your Network Traffic Invisible to Hackers with SSHepherd
Traditional security measures like firewalls and encryption play a critical role, but they aren’t enough. If… 04.09.25
04.09.25How to Make MySQL Databases Invisible to Hackers with SSHepherd
When it comes to securing MySQL databases, most organizations are focused on encryption, firewalls, and authentication… 03.14.25
03.14.25Making Your Websites Invisible to Hackers, Bots, and AI
As cybersecurity threats become more sophisticated, businesses of all sizes face an ongoing challenge: how do… 02.12.25
02.12.25Revolutionize GPO Management: Preparing for AGPM’s End-of-Life and Beyond
As enterprises navigate the evolving landscape of IT infrastructure management, a significant milestone approaches that demands… 01.15.25
01.15.25How SSHepherd® Locks Down SSH Ports and Reduces Cybersecurity Risks
Cybersecurity professionals face an ongoing challenge: balancing the accessibility of network systems with the need to… 12.11.24
12.11.24Invisible Fortresses: Securing Microsoft IIS Servers with SSHepherd
Microsoft Internet Information Services (IIS) powers countless critical web applications, from e-commerce platforms to internal business… 11.14.24
11.14.24Invisible Fortresses: How SSHepherd Revolutionizes SFTP Server Security
In today’s digital landscape, the security of file transfers is paramount for organizations across all industries.… 10.17.24
10.17.24UPA’s Role-Based GPO Change Management: Flexible, Offline, and Mission Critical
With the growing demand for cross-platform consistency and security, Universal Policy Administrator (UPA) steps in as…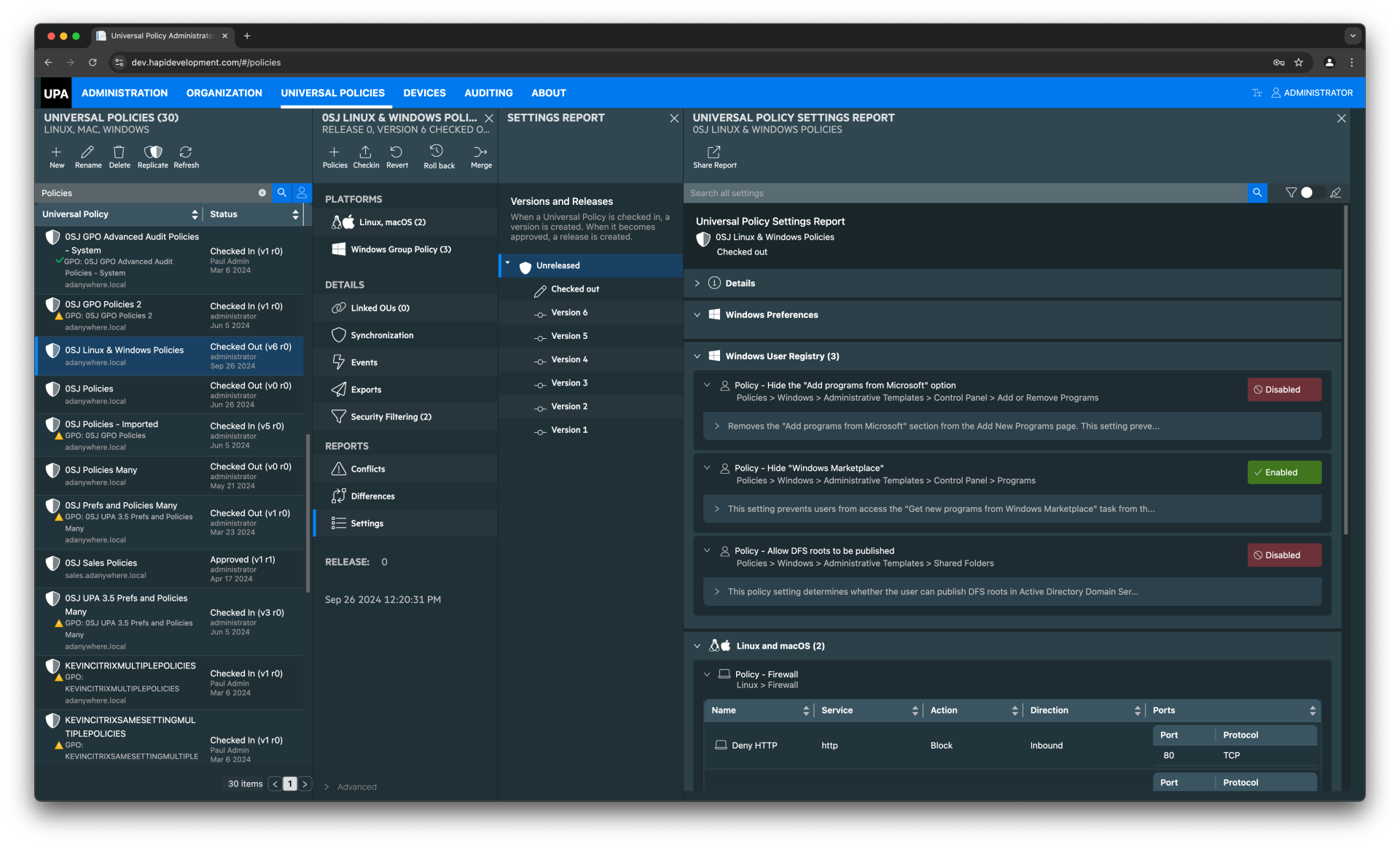 09.27.24
09.27.24The Evolution of Microsoft Active Directory Group Policy Objects and the Future of GPO Management
The Advent and History of Group Policy Objects Introduced with Windows 2000, Group Policy Objects (GPOs)… 08.30.24
08.30.24Introduction to Linux Security Risks
Linux serves as the backbone behind most of the internet. Its widespread use makes it a… 08.14.24
08.14.24Understanding Insider Threats and How to Stop Them with SSHepherd
Insider threats pose one of the most challenging security risks for organizations today. Unlike external attacks,… 07.26.24
07.26.24Enhancing Cybersecurity with SSHepherd: A Comprehensive Mapping to NIST 800-53 Controls
SSHepherd, a powerful cybersecurity product, offers a range of features that map directly to multiple control… 07.14.24
07.14.24How to Make Your Windows RDP Environment Invisible to Hackers
In today’s world, securing your Remote Desktop Protocol (RDP) environment is crucial. Hackers constantly scan for… 06.25.24
06.25.24The MITRE ATT&CK Framework and SSHepherd®
SSHepherd provides robust defense across the entire MITRE ATT&CK Framework by closing the very ports that… 06.12.24
06.12.24Securing Your Network by Identifying and Mitigating Open Ports
Understanding the open port attack surface is crucial for securing your network. In this blog, we’ll… 05.28.24
05.28.24Contain Phishing Exploits and Stop Ransomware Attacks
In today’s digital age, cybersecurity is under constant threat. The ability to contain a phishing exploit… 04.09.25
04.09.25Make Your Network Traffic Invisible to Hackers with SSHepherd
Traditional security measures like firewalls and encryption play a critical role, but they aren’t enough. If… 04.09.25
04.09.25How to Make MySQL Databases Invisible to Hackers with SSHepherd
When it comes to securing MySQL databases, most organizations are focused on encryption, firewalls, and authentication… 03.14.25
03.14.25Making Your Websites Invisible to Hackers, Bots, and AI
As cybersecurity threats become more sophisticated, businesses of all sizes face an ongoing challenge: how do… 02.12.25
02.12.25Revolutionize GPO Management: Preparing for AGPM’s End-of-Life and Beyond
As enterprises navigate the evolving landscape of IT infrastructure management, a significant milestone approaches that demands… 01.15.25
01.15.25How SSHepherd® Locks Down SSH Ports and Reduces Cybersecurity Risks
Cybersecurity professionals face an ongoing challenge: balancing the accessibility of network systems with the need to… 12.11.24
12.11.24Invisible Fortresses: Securing Microsoft IIS Servers with SSHepherd
Microsoft Internet Information Services (IIS) powers countless critical web applications, from e-commerce platforms to internal business… 11.14.24
11.14.24Invisible Fortresses: How SSHepherd Revolutionizes SFTP Server Security
In today’s digital landscape, the security of file transfers is paramount for organizations across all industries.… 10.17.24
10.17.24UPA’s Role-Based GPO Change Management: Flexible, Offline, and Mission Critical
With the growing demand for cross-platform consistency and security, Universal Policy Administrator (UPA) steps in as… 09.27.24
09.27.24The Evolution of Microsoft Active Directory Group Policy Objects and the Future of GPO Management
The Advent and History of Group Policy Objects Introduced with Windows 2000, Group Policy Objects (GPOs)… 08.30.24
08.30.24Introduction to Linux Security Risks
Linux serves as the backbone behind most of the internet. Its widespread use makes it a… 08.14.24
08.14.24Understanding Insider Threats and How to Stop Them with SSHepherd
Insider threats pose one of the most challenging security risks for organizations today. Unlike external attacks,… 07.26.24
07.26.24Enhancing Cybersecurity with SSHepherd: A Comprehensive Mapping to NIST 800-53 Controls
SSHepherd, a powerful cybersecurity product, offers a range of features that map directly to multiple control… 07.14.24
07.14.24How to Make Your Windows RDP Environment Invisible to Hackers
In today’s world, securing your Remote Desktop Protocol (RDP) environment is crucial. Hackers constantly scan for… 06.25.24
06.25.24The MITRE ATT&CK Framework and SSHepherd®
SSHepherd provides robust defense across the entire MITRE ATT&CK Framework by closing the very ports that… 06.12.24
06.12.24Securing Your Network by Identifying and Mitigating Open Ports
Understanding the open port attack surface is crucial for securing your network. In this blog, we’ll… 05.28.24
05.28.24Contain Phishing Exploits and Stop Ransomware Attacks
In today’s digital age, cybersecurity is under constant threat. The ability to contain a phishing exploit… 04.09.25
04.09.25Make Your Network Traffic Invisible to Hackers with SSHepherd
Traditional security measures like firewalls and encryption play a critical role, but they aren’t enough. If… 04.09.25
04.09.25How to Make MySQL Databases Invisible to Hackers with SSHepherd
When it comes to securing MySQL databases, most organizations are focused on encryption, firewalls, and authentication… 03.14.25
03.14.25Making Your Websites Invisible to Hackers, Bots, and AI
As cybersecurity threats become more sophisticated, businesses of all sizes face an ongoing challenge: how do… 02.12.25
02.12.25Revolutionize GPO Management: Preparing for AGPM’s End-of-Life and Beyond
As enterprises navigate the evolving landscape of IT infrastructure management, a significant milestone approaches that demands… 01.15.25
01.15.25How SSHepherd® Locks Down SSH Ports and Reduces Cybersecurity Risks
Cybersecurity professionals face an ongoing challenge: balancing the accessibility of network systems with the need to… 12.11.24
12.11.24Invisible Fortresses: Securing Microsoft IIS Servers with SSHepherd
Microsoft Internet Information Services (IIS) powers countless critical web applications, from e-commerce platforms to internal business… 11.14.24
11.14.24Invisible Fortresses: How SSHepherd Revolutionizes SFTP Server Security
In today’s digital landscape, the security of file transfers is paramount for organizations across all industries.… 10.17.24
10.17.24UPA’s Role-Based GPO Change Management: Flexible, Offline, and Mission Critical
With the growing demand for cross-platform consistency and security, Universal Policy Administrator (UPA) steps in as… 09.27.24
09.27.24The Evolution of Microsoft Active Directory Group Policy Objects and the Future of GPO Management
The Advent and History of Group Policy Objects Introduced with Windows 2000, Group Policy Objects (GPOs)… 08.30.24
08.30.24Introduction to Linux Security Risks
Linux serves as the backbone behind most of the internet. Its widespread use makes it a… 08.14.24
08.14.24Understanding Insider Threats and How to Stop Them with SSHepherd
Insider threats pose one of the most challenging security risks for organizations today. Unlike external attacks,… 07.26.24
07.26.24Enhancing Cybersecurity with SSHepherd: A Comprehensive Mapping to NIST 800-53 Controls
SSHepherd, a powerful cybersecurity product, offers a range of features that map directly to multiple control… 07.14.24
07.14.24How to Make Your Windows RDP Environment Invisible to Hackers
In today’s world, securing your Remote Desktop Protocol (RDP) environment is crucial. Hackers constantly scan for… 06.25.24
06.25.24The MITRE ATT&CK Framework and SSHepherd®
SSHepherd provides robust defense across the entire MITRE ATT&CK Framework by closing the very ports that… 06.12.24
06.12.24Securing Your Network by Identifying and Mitigating Open Ports
Understanding the open port attack surface is crucial for securing your network. In this blog, we’ll… 05.28.24
05.28.24Contain Phishing Exploits and Stop Ransomware Attacks
In today’s digital age, cybersecurity is under constant threat. The ability to contain a phishing exploit…
- darkreading.comHow Active Directory Bridging Extends Security Automation to Hybrid IT EnvironmentsRead More
- techtarget.comAttackers discovering exposed cloud assets within minutesRead More
- candid.technology
 P2Pinfect expands to 32-bit MIPS processors in escalating threatRead More
P2Pinfect expands to 32-bit MIPS processors in escalating threatRead More - darkreading.comNorth Korea's Kimsuky Doubles Down on Remote Desktop ControlRead More
- siliconangle.com
 Remote Desktop Protocol exposures leave 85% of organizations vulnerable to attackRead More
Remote Desktop Protocol exposures leave 85% of organizations vulnerable to attackRead More - itjungle.com
 Midsummer Security Indicators: Hot and GloomyRead More
Midsummer Security Indicators: Hot and GloomyRead More - darkreading.comHow Active Directory Bridging Extends Security Automation to Hybrid IT EnvironmentsRead More
- techtarget.comAttackers discovering exposed cloud assets within minutesRead More
- candid.technology
 P2Pinfect expands to 32-bit MIPS processors in escalating threatRead More
P2Pinfect expands to 32-bit MIPS processors in escalating threatRead More - darkreading.comNorth Korea's Kimsuky Doubles Down on Remote Desktop ControlRead More
- siliconangle.com
 Remote Desktop Protocol exposures leave 85% of organizations vulnerable to attackRead More
Remote Desktop Protocol exposures leave 85% of organizations vulnerable to attackRead More - itjungle.com
 Midsummer Security Indicators: Hot and GloomyRead More
Midsummer Security Indicators: Hot and GloomyRead More - darkreading.comHow Active Directory Bridging Extends Security Automation to Hybrid IT EnvironmentsRead More
- techtarget.comAttackers discovering exposed cloud assets within minutesRead More
- candid.technology
 P2Pinfect expands to 32-bit MIPS processors in escalating threatRead More
P2Pinfect expands to 32-bit MIPS processors in escalating threatRead More - darkreading.comNorth Korea's Kimsuky Doubles Down on Remote Desktop ControlRead More
- siliconangle.com
 Remote Desktop Protocol exposures leave 85% of organizations vulnerable to attackRead More
Remote Desktop Protocol exposures leave 85% of organizations vulnerable to attackRead More - itjungle.com
 Midsummer Security Indicators: Hot and GloomyRead More
Midsummer Security Indicators: Hot and GloomyRead More
Contact Us
Please contact us to learn how Full Armor can help to protect your IT infrastructure.
Our team of security experts is ready to help you implement the right solutions for your enterprise.






