
Introduction to Linux Security Risks
Linux serves as the backbone behind most of the internet. Its widespread use makes it a prime target for hackers aiming to exploit vulnerabilities. One of the significant tools hackers use to identify these vulnerabilities is Shodan, often referred to as the “Hacker’s Search Engine.”
Shodan: The Hacker’s Search Engine
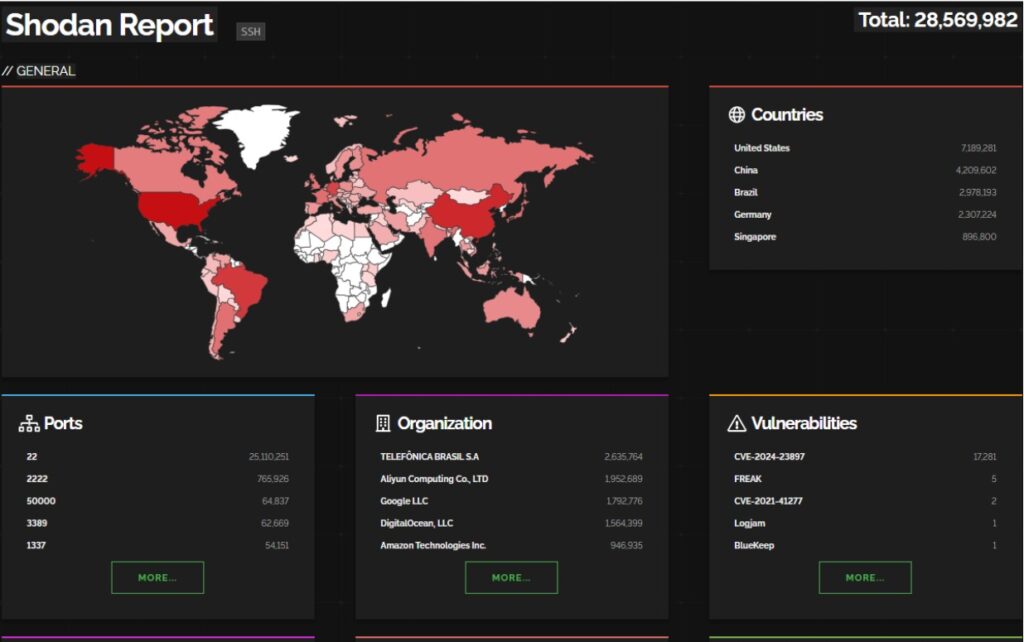
Shodan is a powerful internet search engine that allows users to discover devices connected to the internet by scanning for open ports. While it has legitimate uses for network administrators and researchers, hackers often exploit it to find unprotected Linux servers with open SSH ports. For instance, a recent search for ‘SSH’ on Shodan revealed over 28 million open ports, highlighting the scale of potential vulnerabilities.
The History and Purpose of Open Ports
Open ports have been an essential part of networking since the early days of the internet. They allow services and applications to communicate with each other over a network. For example, open ports enable web servers to accept requests from web browsers, email servers to receive emails, and SSH servers to allow remote administration.
Benefits of Open Ports:
- Facilitating Communication: Open ports enable various network services to communicate effectively, which is crucial for the functionality of many internet-based applications.
- Remote Management: Open ports, such as SSH, allow administrators to manage servers remotely, providing flexibility and convenience.
- Service Accessibility: They make services accessible to users and other systems, ensuring the smooth operation of online services and applications.
However, the very features that make open ports useful also make them vulnerable to exploitation.
The Risks of Open SSH Ports
While open ports are necessary for certain functionalities, they also pose significant security risks. Open SSH ports, in particular, can be a gateway for hackers. These open doors invite unauthorized access, allowing cyber intruders to exploit any weaknesses in security protocols.
Hackers use tools like Shodan to scan the internet for open ports, identifying unprotected Linux servers as potential targets. Once they find an open server, they will exploit any vulnerabilities to gain control, potentially causing significant harm. A hacker gaining access to an open SSH port could perform a variety of malicious activities, such as:
- Data Theft: Stealing sensitive information stored on the server.
- Server Hijacking: Taking control of the server to use it for further attacks, such as launching DDoS attacks or spreading malware.
- Data Corruption: Modifying or deleting critical data, causing operational disruptions.
- Resource Exploitation: Using server resources for illegal activities, such as cryptomining or hosting malicious content.
Managing the Risk with SSHepherd
Given the necessity of SSH for remote management, how can we mitigate these risks? This is where SSHepherd® comes into play. SSHepherd® is a security tool enabling you to connect to your machines while the ports are closed, making them invisible to hackers and automated scans. By using SSHepherd®, your servers go stealth, accessible to you but hidden from potential attackers.
SSHepherd® adds an important layer of security because if a hacker can find a port, they can attack it. By closing these ports, SSHepherd® prevents hackers from identifying potential entry points, significantly reducing the risk of unauthorized access.
The Benefits of SSHepherd®
- Enhanced Security: SSHepherd® ensures your Linux servers are secure by closing open SSH ports, reducing the risk of unauthorized access. This proactive measure is crucial because open ports are potential gateways for attackers.
- Stealth Mode: Your servers become invisible to hackers, effectively protecting them from being targeted. Closed ports mean that even if a hacker is scanning for vulnerabilities, they will not find any open ports to exploit.
- Peace of Mind: With SSHepherd®, you can rest assured that your servers are out of sight and out of mind for those with malicious intent. This invisibility is a powerful deterrent, ensuring that hackers cannot identify and target your servers.
By integrating SSHepherd® into your security strategy, you add a critical layer of defense that keeps your network secure and your data protected.
Conclusion
In the world of cybersecurity, proactive measures are crucial. Open SSH ports on Linux servers present a significant risk, but tools like SSHepherd® provide an effective solution. By making your servers invisible to hackers, SSHepherd® helps you maintain the security and integrity of your systems.
For more information on how SSHepherd® can protect your Linux servers, check out the videos below:
Secrets to Secure Your Linux System
SSHepherd® SSH demo
