Every day, cybercriminals are scanning the internet for vulnerable entry points into corporate networks. While security teams focus on patching software vulnerabilities and updating firewalls, two of the most dangerous attack vectors remain wide open on critical servers across organizations worldwide: RDP and SSH ports.
The Most Attacked Ports You’re Still Using
Remote Desktop Protocol (RDP) and Secure Shell (SSH) services are essential tools for system administrators. They enable remote access to servers and virtual machines for routine maintenance, configuration changes, file transfers, and script execution. However, these same capabilities that make them indispensable also make them prime targets for attackers.
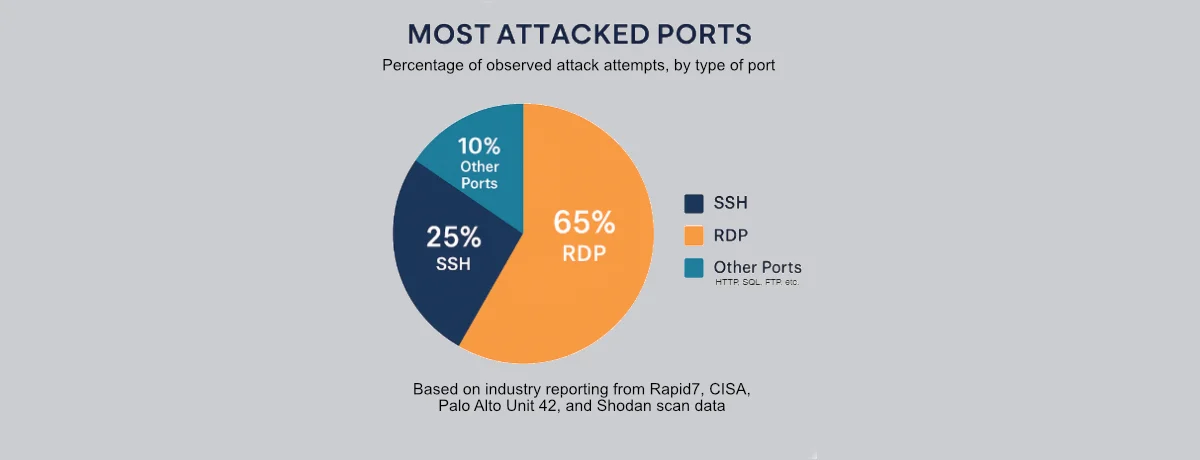
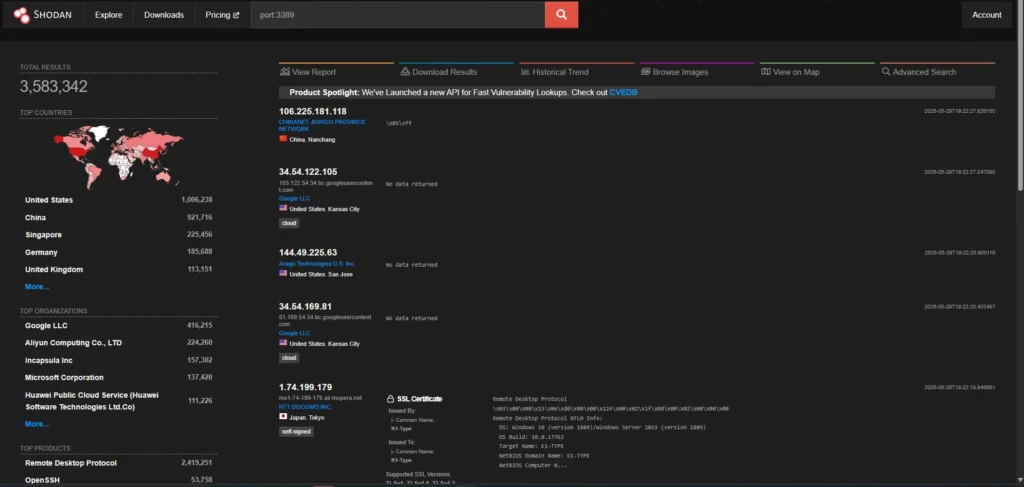
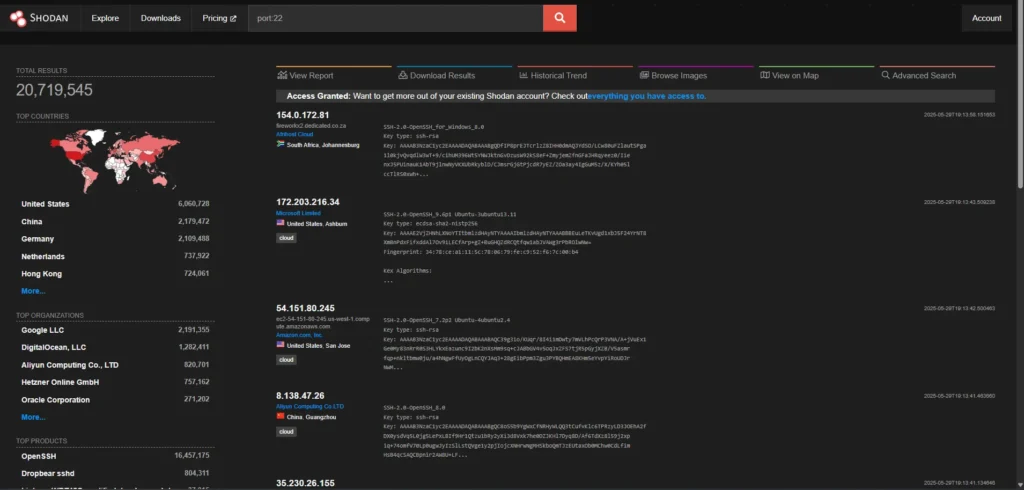
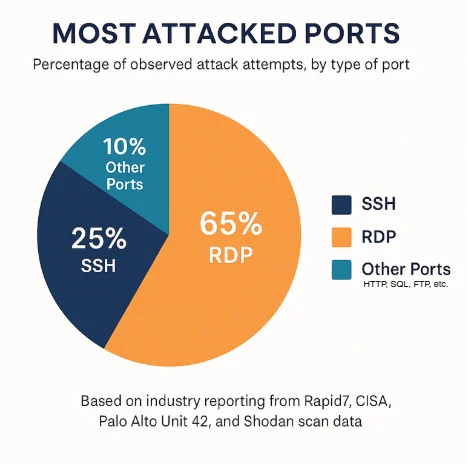
Industry reports consistently identify RDP and SSH as the most frequently attacked ports on the internet. Recent Shodan scans reveal the staggering scope of this exposure: over 3.5 million systems worldwide have RDP port 3389 openly accessible, while an alarming 20+ million systems expose SSH port 22 to the internet. The reason these numbers are so concerning is simple yet alarming: these protocols provide direct remote access to operating systems. When hackers successfully compromise these services, they gain the keys to the kingdom – complete control over your critical infrastructure.
Why Traditional Security Measures Fall Short
The fundamental problem lies in how these services operate. RDP and SSH ports are often publicly exposed to the internet, making them easily discoverable through common network scans. When attackers probe these ports, the services readily reveal information about the underlying systems, essentially providing hackers with a roadmap for their attack.
Consider the typical attack progression: once adversaries discover open RDP or SSH ports, they launch targeted attacks against these services. With millions of exposed systems acting as potential entry points, attackers have an abundance of targets to choose from. If the attacker is an internal threat – perhaps a disgruntled employee with existing credentials – the situation becomes even more dangerous. They can leverage these access points to escalate privileges and move laterally throughout the network, potentially accessing sensitive data and critical systems far beyond their original scope of access.
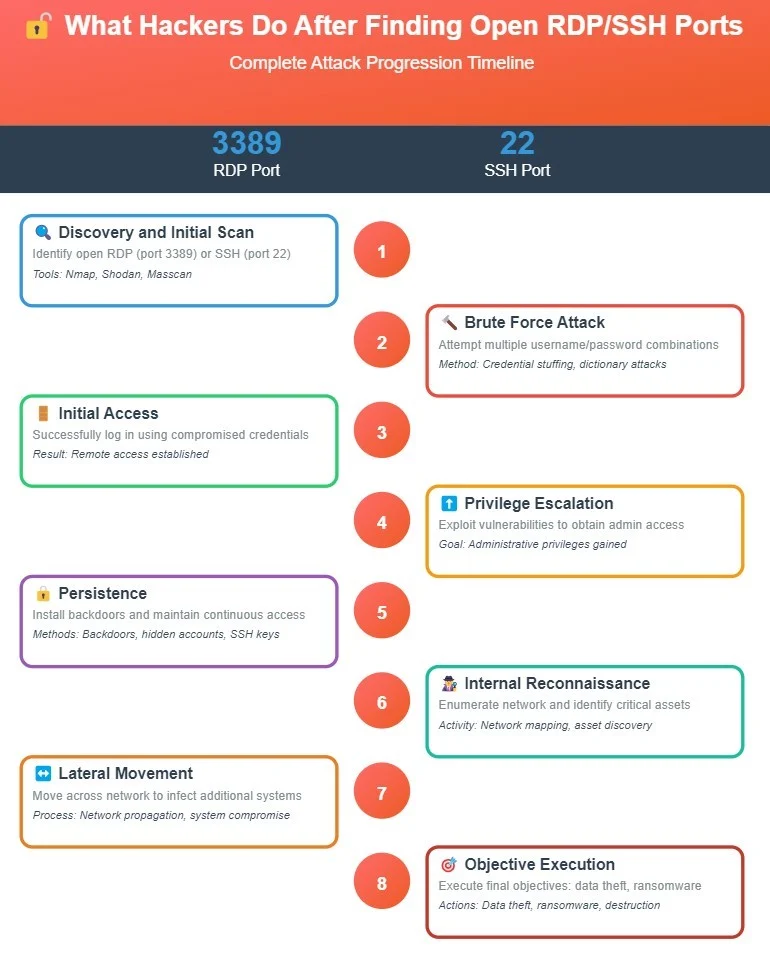
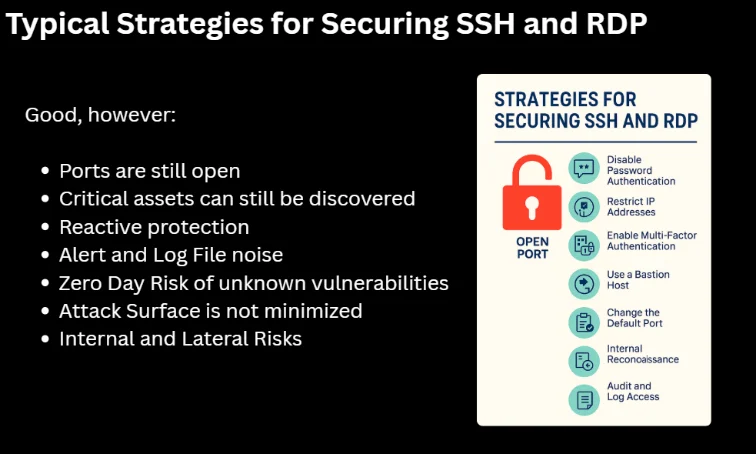
Security administrators have developed numerous strategies to harden RDP and SSH services, including implementing strong authentication, network segmentation, and access controls. While these measures are valuable and should remain part of any comprehensive security strategy, they don’t address the core vulnerability: the ports themselves remain visible and accessible to attackers.
The SSHepherd® Solution: Security Through Invisibility
This is where SSHepherd® revolutionizes server security. Rather than simply hardening existing RDP and SSH services, SSHepherd® eliminates the attack vector entirely by making these critical ports invisible to potential attackers.
With SSHepherd® deployed across your servers and virtual machines, your system administrators retain full functionality – they can still run complete RDP and SSH sessions with all the capabilities they need for system management. The crucial difference is that hackers scanning your network will never know these services exist.
By removing RDP and SSH ports from the visible attack surface, SSHepherd® doesn’t just reduce your risk – it eliminates entire categories of attacks. Automated scanning tools that search for vulnerable RDP and SSH services will find nothing. Targeted attacks against these protocols become impossible when attackers can’t locate the services in the first place.
Protecting What Matters Most
In today’s threat landscape, security through obscurity isn’t enough – but security through invisibility, combined with robust access controls and monitoring, creates a powerful defensive strategy. SSHepherd® allows organizations to maintain the operational flexibility they need while dramatically reducing their exposure to some of the most common and dangerous attack vectors in cybersecurity.
The question isn’t whether your RDP and SSH ports will be attacked – it’s whether attackers will be able to find them in the first place.
