
For decades, the cybersecurity narrative has been dominated by a single villain: the phishing email. We’ve spent billions on employee training, telling teams not to click the link or download the attachment. But as we move through 2026, the data shows a startling shift in the battlefield.
Hackers aren’t just “hacking the human” anymore; they are increasingly bypassing the user entirely by targeting the very infrastructure we use to connect.
The Rise of the “Invisible” Entry Point
According to the 2025 Verizon Data Breach Investigations Report (DBIR), vulnerability exploitation—the act of targeting unpatched software and open network ports—has surged by 34%. For the first time, this technical vector is nearly tied with credential abuse as the most common way hackers gain initial access to a network.
Even more alarming is the focus on edge devices. The exploitation of vulnerabilities in VPNs, firewalls, and routers increased nearly eight-fold last year. These devices are the “front doors” of your network, and because they are designed to be discoverable so that connections can be established, they are permanent targets for automated AI scanners.

The Fundamental Flaw: Firewalls & VPNs Need Open Ports
This is where conventional wisdom falls short. Many organizations invest heavily in perimeter defenses like next-generation firewalls and VPN gateways, believing they offer a complete solution. However, these tools, by their very nature, must expose ports to the internet to function.
- Firewalls: Stand guard over a visible entry point. They don’t make the port invisible; they just filter who can see it.
- VPNs: Must have an open port (like TCP 443) exposed to the internet to listen for remote users.
In essence, while these tools are crucial, they inherently create the “discoverable” surface that modern attackers are now relentlessly exploiting.

The Mathematical Trap: Chance vs. Certainty from the Attacker’s Perspective
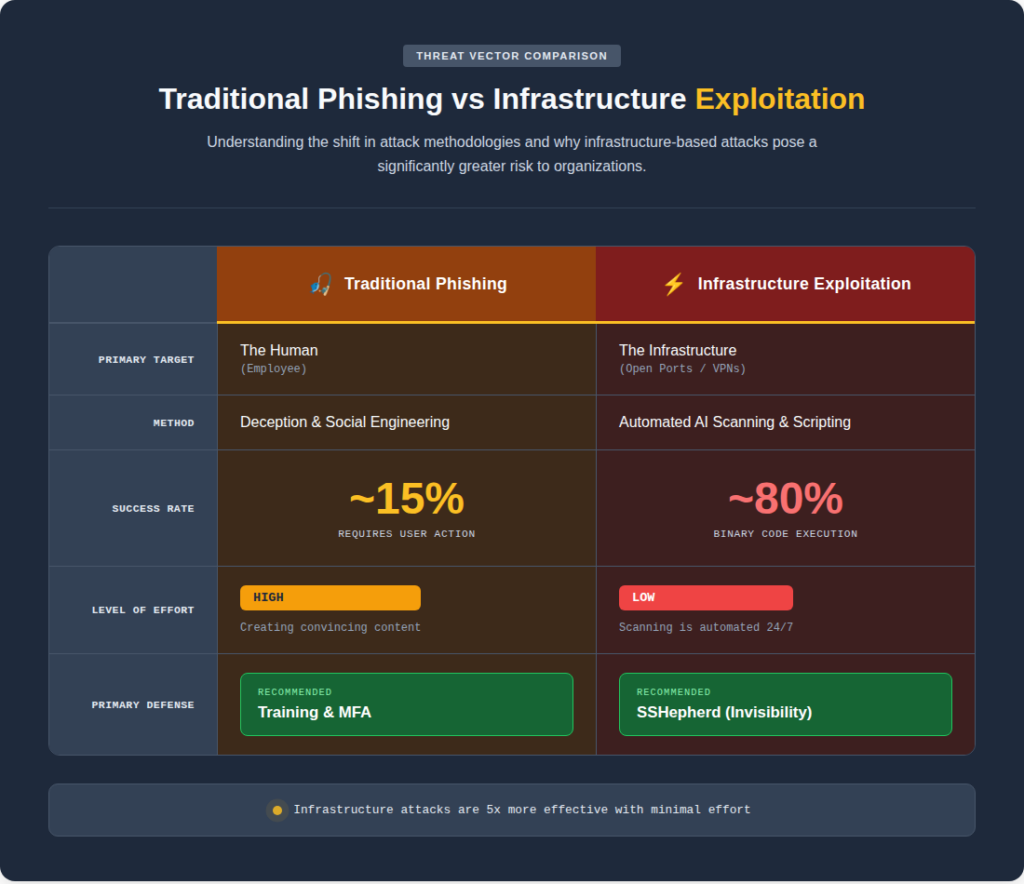
To understand why the industry is shifting its focus, we have to look at the “Success Rate” of an attack. When a hacker sends a phishing campaign, they are playing a game of probability. Industry data suggests a ~15% success rate per campaign; they need to bypass human intuition and MFA.
However, when a hacker targets infrastructure, the math changes. Once an automated scanner identifies an open port with a critical vulnerability, research from Rapid7 and Palo Alto Networks (Unit 42) indicates the exploitation success rate jumps to nearly 80%.
Unlike a human, who might have a “gut feeling” a link is fake, a software vulnerability is binary. If the port is discoverable and the vulnerability exists, the exploit code executes. In this scenario, discovery equals compromise.
The Zero Trust Solution: Making the Network Disappear
The industry is moving toward a “Zero Trust” model, but traditional Zero Trust often focuses only on identity. SSHepherd® takes this a step further by introducing Network Invisibility.
SSHepherd® is a patented technology that enables full network connectivity without exposing a single port to the public internet. It shifts the paradigm from “detect and defend” to “remove and secure.”
- Hackers See Nothing: By closing ports, you remove the target. If a scanner can’t find a port, it can’t launch an exploit.
- Authorized Access Only: Connectivity is only established after authentication.
- Silence the Noise: Event logs go from thousands of “probes” to zero.
The Data-Backed Advantage
The impact of moving to an invisible architecture is measurable:
- 78% Reduction in Breach Risk: By eliminating the most aggressive growth vector.
- 90% Drop in Security Incidents: By removing the “low-hanging fruit” of open ports.
Conclusion: Stop Defending, Start Disappearing
As we look at the 2026 threat landscape, one thing is clear: the “castle and moat” is dead. You cannot defend a door that everyone can see. By making your network invisible with SSHepherd, you aren’t just building a better wall—you’re removing the target entirely.
References
- Verizon 2025 DBIR: Vulnerability Trends
- Rapid7 / Unit 42: Vulnerability Intelligence Reports
- IBM X-Force 2025: Threat Intelligence Index
- Qualys: Edge Device Exploitation Stats
