Insider threats pose one of the most challenging security risks for organizations today. Unlike external attacks, insider threats come from within the organization, making them particularly difficult to detect and mitigate. According to the Cybersecurity and Infrastructure Security Agency (CISA), Zero Trust principles suggest that we must assume our network has already been penetrated by an adversary. This adversary could be a disgruntled employee, a contractor with remote access privileges, or an external actor who has successfully infiltrated the network, possibly through a phishing campaign. Once inside, this adversary becomes a rogue insider, capable of causing significant damage.
The Rogue Insider’s Process
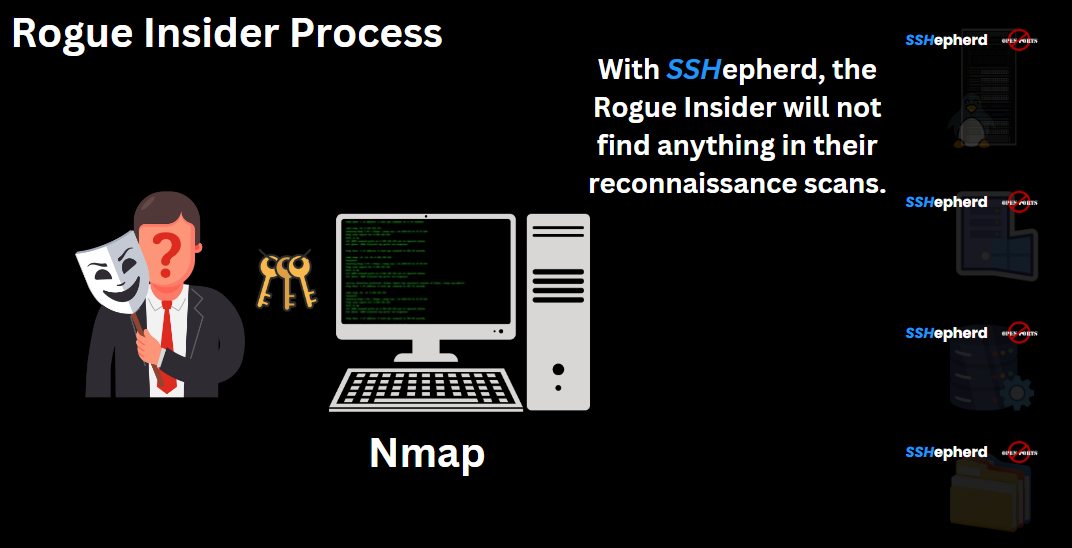
Scenario 1: Unprotected Network
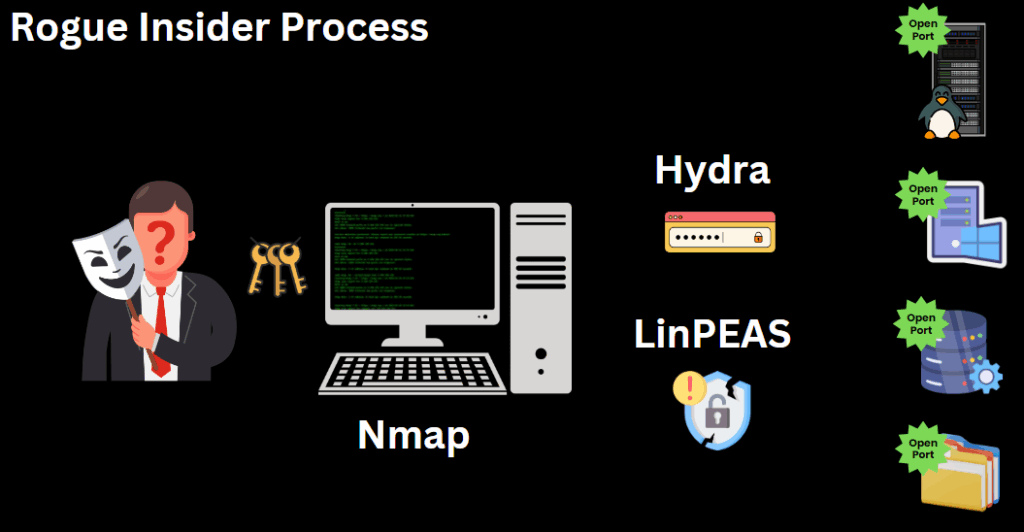
In a typical scenario, a rogue insider with network credentials may use several hacking tools to identify valuable resources. One of the most common tools is Nmap, a network scanning tool that locates services and applications with open, listening ports. Once the insider identifies these services, they can employ tools like Hydra to attempt password cracking and LinPEAS on Linux to identify vulnerabilities and facilitate lateral movement within the network.
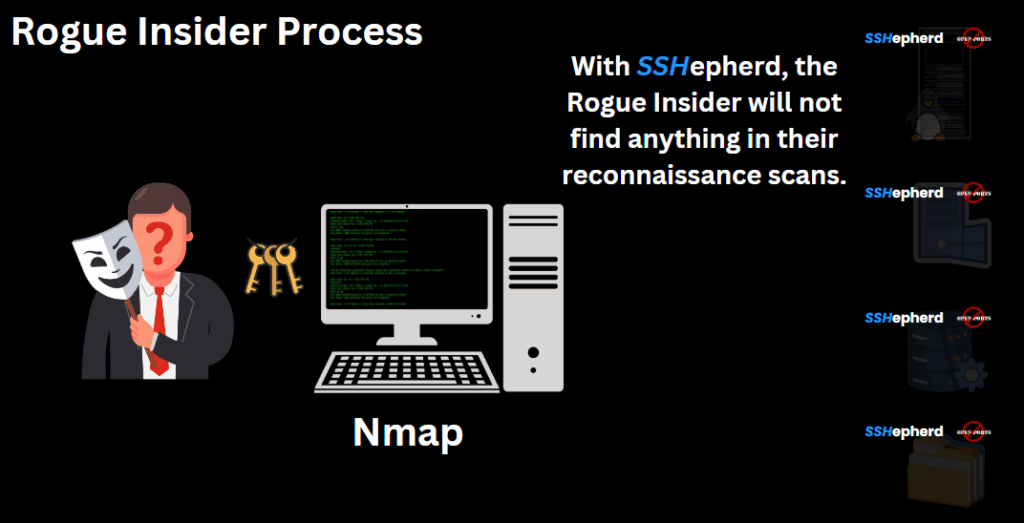
Scenario 2: Network Protected by SSHepherd
In the second scenario, we introduce SSHepherd as a protective measure. With SSHepherd in place, when the rogue insider runs Nmap, they will not find any services or applications because the ports are closed and invisible to the network. This makes it significantly harder for the insider to identify targets and launch attacks.
Scenario 3: Rogue Insider as a SSHepherd User
Even in cases where the rogue insider is a SSHepherd user, the integration of SSHepherd with monitoring tools like Splunk can stop unauthorized activities in real-time. Let’s delve into how this integration works to protect the network.
Real-Time Defense with SSHepherd and Splunk
SSHepherd’s integration with Splunk provides a powerful defense mechanism against insider threats. Here’s how the workflow operates:
- Detection of Unauthorized Applications: The rogue user, also a SSHepherd user, connects to a machine through SSHepherd and runs an unauthorized application like Nmap. Splunk is configured to watch for this event and trigger an action.
- Immediate Action: Upon detecting the unauthorized application, Splunk runs a script that instructs SSHepherd to immediately terminate the session and prevent the user from reconnecting.

- Demonstration on Linux and Windows:
- Linux Environment: In the SSHepherd administrator console, a user named ‘rogue’ has access to both an Ubuntu and a Windows 10 machine. The rogue user runs a SSHepherd SSH session to connect to the Ubuntu machine. Splunk, configured to watch for Nmap, immediately sees the unauthorized activity, generates an event in real-time, and triggers SSHepherd to terminate the session. The rogue user is then removed from the Ubuntu machine, preventing further access.
- Windows Environment: The rogue user attempts an RDP session with SSHepherd and runs Zenmap (the Windows version of Nmap). Splunk detects this unauthorized activity, generates an event, and triggers SSHepherd to terminate the RDP session. The rogue user is unable to reconnect, and the session recording shows the unauthorized activity right before termination.
SSHepherd: A Key Component of Zero Trust Security
SSHepherd plays a crucial role in a multi-layered security strategy within the Zero Trust framework. It enforces least privilege, role-based access control, session monitoring, and the termination of unauthorized activities. By integrating with monitoring tools like Splunk, SSHepherd provides real-time defense against insider threats, ensuring that even trusted users cannot exploit their access for malicious purposes.
